In previous post, we learned how to do end user set up in Hygieia with screenshots. In the current post, we can discuss what is collector in Hygieia and what are the collectors available in Hygieia.
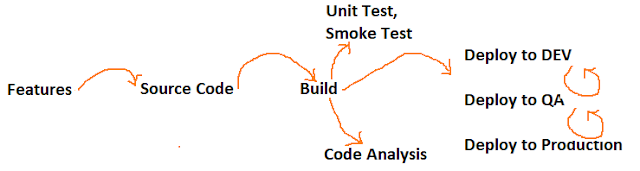
The collector in Hygieia fetches the data from the DevOps tools and saves into MongoDB database. Hygieia uses MongoDB as the database for storage and retrieval of data.
Generally, you can run the collectors using the following command,
- What is Collector in Hygieia ?
The collector in Hygieia fetches the data from the DevOps tools and saves into MongoDB database. Hygieia uses MongoDB as the database for storage and retrieval of data.
For each collector, data saves different mongodb collection, e.g bitbucket data will save into commits collection, bamboo build data will save into builds collection and udeploy environment data will save into environment_component collection.
- How to run Collector in Hygieia ?
Generally, you can run the collectors using the following command,
java -jar <Path to collector-name.jar> --spring.config.name=<prefix for properties> --spring.config.location=<path to properties file location>
You may choose the collectors applicable to your DevOps toolset from the list of supported collectors. In addition, you may write your own collector and plug it in to match your DevOps toolset.
- Supported Collectors
Hygieia supports the following collectors:
- Build Collectors - Jenkins, Bamboo, Jenkins-codequality, Jenkins Cucumber & Sonar
- Cloud Collectors - AWS.
- Deploy Collectors - uDeploy, XLDeploy
- Feature Collectors - Jira, VersionOne, Gitlab & Rally.
- Miscellaneous Collectors - Chat Ops & Score.
- SCM Collectors - Bitbucket, GitHub, Gitlab, Subversion & GitHub GraphQL.
- Performance Collector - AppDynamics.
- Configuration Management Database (CMDB) - HP Service Manager (HPSM).
- Library Policy - Nexus IQ.
- Artifact Repository - Artifactory.
- Creation of Encrypted Key for private Repo's
Encryption for private repositories requires that you generate a secret key and add it to your repository settings files. The steps for encrypting private repositories are as follows,
Step 1: From the core module, generate a secret key.
java -jar <path-to-jar>/core-2.0.5-SNAPSHOT.jar com.capitalone.dashboard.util.Encryption
Step 2: Add the generated key to the API properties file.
api.properties
key=<your-generated-key>
Step 3: Add that same generated key to your repository settings file. This key is required for the target collector to decrypt your saved repository password.
For example, if your repo is GitHub, add the following to the github.properties file:
github.properties,
github.key=<your-generated-key>
Related Posts:--